Your Phone Is Watching You Right Now — Here’s How to Prove It
November 13 | Posted by mrossol | 1st Amendment, Deep State, Intelligence Services, Losing Freedom, TechnologyI do believe this kind of surveillance is there. How best to avoid? Don’t travel with smart devices. Of course, these surveillance cells can pick up your laptop too, but if you are just home…? mrossol
Source: Your Phone Is Watching You Right Now — Here’s How to Prove It
In partnership with Anonymous Media Group and the The Dirty Dozen Dispatch, we are delighted to debut an exclusive exposé that digs beneath the surface of the narratives shaping our world. This piece isn’t just another story, it’s a challenge to complacency, a call to question, and a deep dive into the truths too often buried by convenience and control.
What if I told you that your smartphone is broadcasting your exact location to a secret surveillance network 24/7, even when it’s turned off? What if this system can track not just where you go, but who you meet with, how long you stay, and predict where you’ll be next? And what if I could show you how to prove this is happening in your own neighborhood with a free app and ten minutes of your time?
Three weeks ago, I was contacted by someone who claimed to have evidence of a global surveillance system. I was skeptical. In an era of conspiracy-theory-psy-ops and digital paranoia, extraordinary claims require extraordinary evidence.
I thought I understood the risks of technology and the state of our world, until what I uncovered showed me just how dangerously wrong I was.
The Message That Started Everything
The first message was simple:
“I hope I have the right individual. I was told by Anonymous Media Group that you want to talk with someone.”
What followed was a weeks-long investigation into what may be the most comprehensive surveillance system ever deployed against civilian populations. The whistleblower, let’s call him “Brutus,” lives in Central America and stumbled onto this discovery while trying to debunk conspiracy theories about COVID vaccines.
Instead of debunking misinformation, he uncovered something far more disturbing: a real surveillance network hiding in plain sight.
What Brutus Found
Brutus is not a professional spy or cybersecurity expert. He’s someone who got curious, downloaded a free Bluetooth scanner app, and started looking at what devices were broadcasting around him. What he found defied explanation:
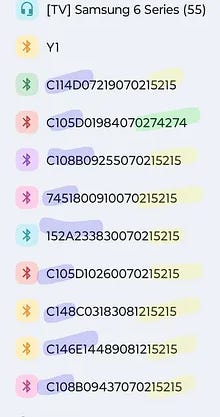
A screenshot from Brutus’ phone showing the BLE scanner app. The highlighted devices are part of the surveillance network. The color-coding, indicates the location of the devices: yellow for his town, green for a neighboring town, and purple for ID status.
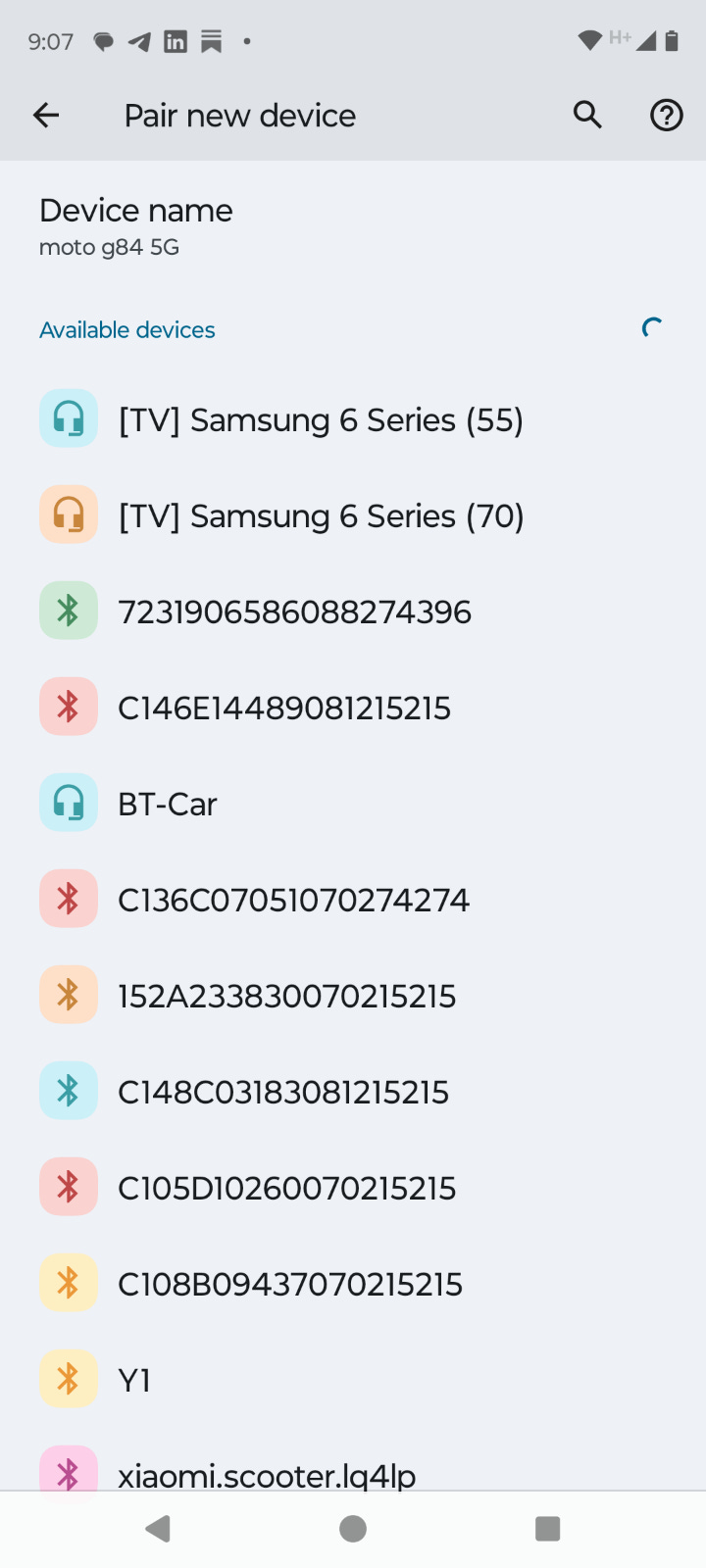
Devices with names like “C108B094370702…” were everywhere. In his small Central American town, at the local bar, in his neighbor’s homes. These weren’t normal Bluetooth devices, they were something else entirely.
They used illegal, unregistered MAC addresses. Every legitimate Bluetooth device must register its identifier with the Institute of Electrical and Electronics Engineers (IEEE). Companies like Samsung pay $10,000 for this registration. These devices showed up as “Unknown” manufacturers, a red flag that they were operating outside federal communications law.
They tracked individual people. Brutus discovered he could identify specific individuals by their device signatures. He knew when “the ugly redhead across from me” was in town (she lives 10 miles away), when people from neighboring towns visited, and could track anyone’s movements in real-time.
The system had geographic encoding. The device names contained area codes, digital zip codes that mapped people to specific neighborhoods or “15-minute zones.” Brutus could tell not just who was where, but which community they belonged to.
Most chilling of all: When his friend “Debby” upgraded her iPhone, all her surveillance tags followed her to the new device. This wasn’t tracking phones, it was tracking people.
The Technical Smoking Gun
Brutus provided screenshots that are nothing short of extraordinary. Using a simple Android app called “BLE Scanner”, he documented:
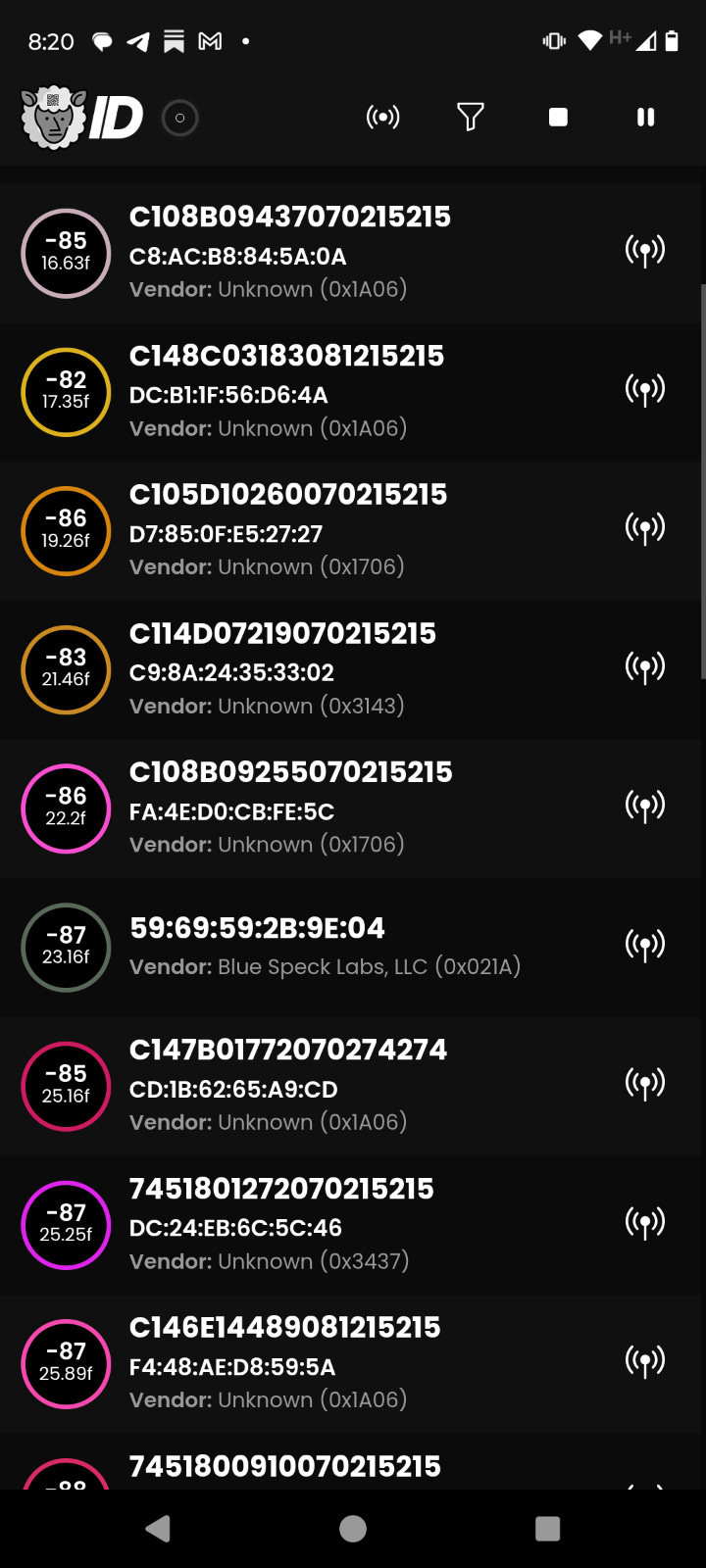
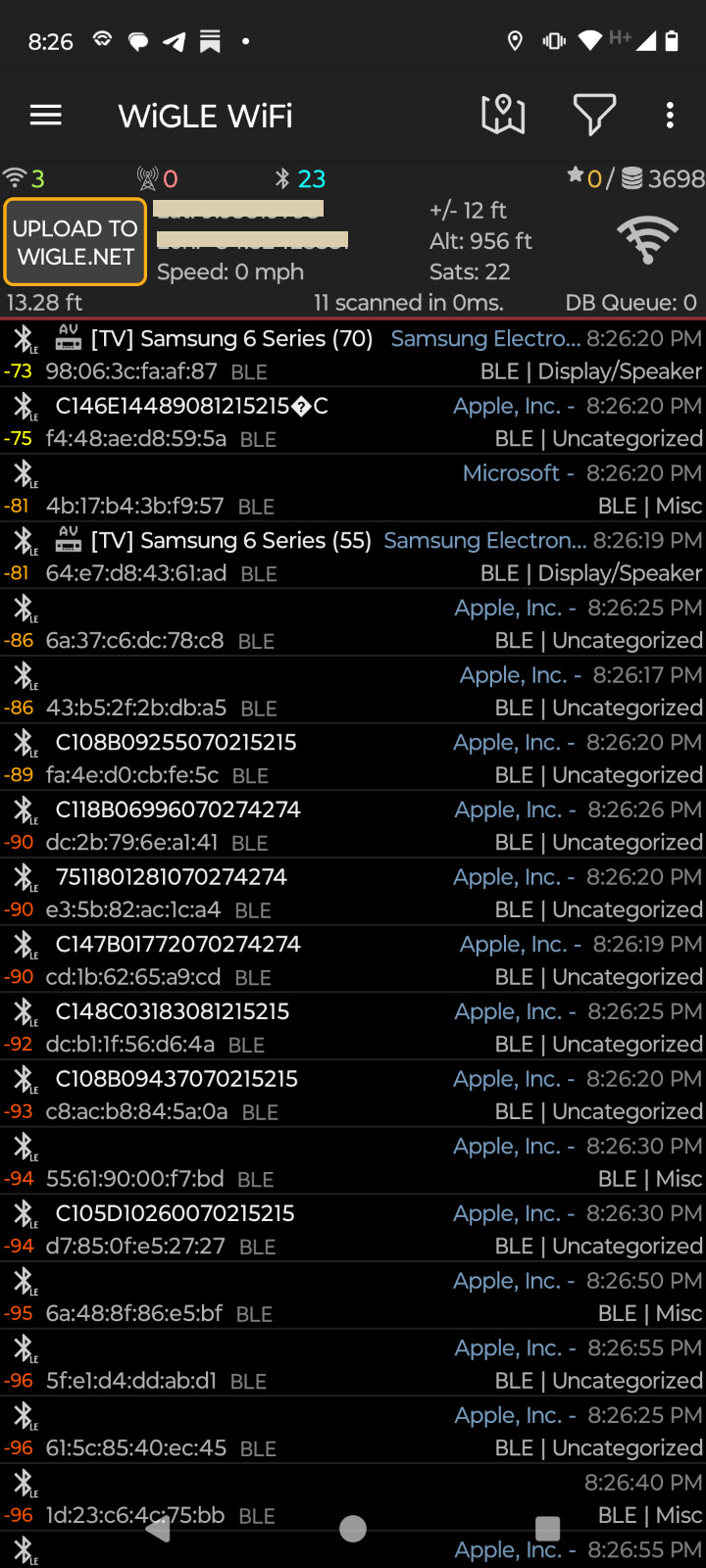
• 23 surveillance devices detected simultaneously in a single location
• All devices attributed to “Apple, Inc.” despite using illegal, unregistered MAC addresses
• Real-time GPS coordinates showing precise location tracking capabilities
• Signal strength measurements strongly suggesting these devices can track people through concrete walls from 300+ feet away
But the most damning evidence came when Brutus shared a technical documentthat revealed the official name of this system: GAEN (Google/Apple Exposure Notification).
This wasn’t some rogue operation. This was a coordinated effort between the world’s largest technology companies.
The official GAEN Bluetooth specification itself admits that the system is designed to prevent tracking by changing the device identifier every 15 minutes. However, Brutus’ findings suggest this privacy feature is either not working as intended or has been bypassed:
A user’s Rolling Proximity Identifier changes on average every 15 minutes, and needs the Temporary Exposure Key to be correlated to a contact. This behavior reduces the risk of privacy loss from broadcasting the identifiers.
The COVID Connection: How We Got Here
Remember COVID contact tracing? In April 2020, Apple and Google announced a “privacy-preserving” partnership to help track virus exposure. The system was supposed to be:
• Voluntary (you had to opt in)
• Temporary (only during the health emergency)
• Anonymous (no personal data collected)
• Local (data stays on your device)
A 2020 Vox article praised the initiative, noting that “keys stay on your device, not a server” and emphasizing the privacy protections built into the system.
Fast-forward to 2025: Brutus’ evidence shows this system never went away. Instead, it evolved into comprehensive population surveillance infrastructure embedded in consumer products from Amazon LED controllers to smart TVs to street lights.
What was promised as a temporary health tool became a permanent tracking system.
The Academic Validation
Brutus’ findings align perfectly with academic research that has largely been ignored by mainstream media. A groundbreaking study by Erik Rye and Dave Levin at the University of Maryland, titled “Surveilling the Masses with Wi-Fi-Based Positioning Systems,” documented how Apple’s Wi-Fi Positioning System could be exploited for mass surveillance. Their findings, which you can read in the link above, are a chilling parallel to the BLE surveillance he uncovered:
“We present several case studies that demonstrate the types of attacks on privacy that Apple’s WPS enables: We track devices moving in and out of war zones (specifically Ukraine and Gaza), the effects of natural disasters (specifically the fires in Maui), and the possibility of targeted individual tracking by proxy, all by remotely geolocating wireless access points.”
The researchers discovered they could harvest the locations of over 2 billion Wi-Fi access points by systematically querying Apple’s servers. When a device asks Apple for the location of one Wi-Fi network, Apple responds with the precise coordinates of up to 400 nearby networks.
This created what the researchers called a “global surveillance capability” that could track the movement of Wi-Fi devices worldwide without ever being physically near them.
The connection to Brutus’ BLE surveillance discovery is clear: Apple and Google have created multiple overlapping tracking systems that work together to monitor population movements with unprecedented precision.
The Military Connection
Brutus kept referencing something called “Palantir Lavender” and describing this as “military-grade shit.” I thought this was hyperbole until I researched the connections.
Palantir Technologies, the data analytics company co-founded by Peter Thiel, has been open about their role in what they call the “kill chain.” Their AI systems were used in Gaza to select targets for military strikes. The same company has a $443 million contract with the CDC for something called a “Common Operating Picture,” a unified surveillance system for population monitoring.
The technical infrastructure Brutus discovered isn’t just similar to military targeting systems, it appears to be the same technology, deployed against civilian populations under the cover of public health and consumer convenience.
The intelligence community connection runs deeper. In-Q-Tel, the CIA’s venture capital arm, has invested over $1.8 billion in surveillance technologies since 1999, including early funding for Palantir. The same agency has funded over 800 companies developing surveillance and defense technologies.
Even more troubling: DARPA launched its Pandemic Prevention Platform (P3) in 2017, three years before COVID, with over $25 million in funding for biological surveillance and tracking systems. This suggests the surveillance infrastructure was planned long before any health emergency.
The Privacy Violations Are Documented
Brutus’ discoveries aren’t isolated incidents. The Markup, an investigative journalism organization, documented how Google’s contact tracing system violated privacy promises almost immediately after deployment.
Their investigation revealed:
• Hundreds of preinstalled apps could access sensitive tracking data
• MAC address collection enabled device identification beyond stated purposes
• The Department of Homeland Security contracted testing of contact tracing privacy violations
• Google refused to fix known privacy violations, claiming they were insufficient severity
This pattern of deployment first, privacy protection never has become the standard operating procedure for surveillance technology companies.
Why This Matters More Than You Think
This isn’t just about privacy. The surveillance system Brutus documented has capabilities that should terrify anyone who values freedom:
Individual Targeting: The system can identify and track specific people in real-time, even predicting where they’ll be next based on behavioral patterns.
Social Network Mapping: By tracking who meets with whom, the system can identify relationships, political associations, and resistance networks.
Population Control: The geographic encoding system divides people into manageable zones for monitoring and control, digital “15-minute cities” where movement can be tracked and restricted.
Economic Leverage: Integration with digital payment systems and social media platforms means surveillance compliance becomes necessary for economic participation.
Predictive Enforcement: AI analysis of movement and behavior patterns enables intervention before “undesirable” activities occur.
This is the infrastructure of a surveillance state that would make the Stasi1jealous, hidden inside the devices we carry voluntarily and the products we buy for convenience.
The Legal Framework Is Clear
The surveillance system Brutus documented violates multiple layers of law:
Federal Communications Commission Violations: Using unregistered MAC addresses violates 47 CFR § 15.1 and related regulations governing unlicensed radio frequency devices. Penalties can reach $100,000 per violation per day.
Privacy Law Violations: The General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA), and similar statutes worldwide prohibit this kind of tracking without explicit consent.
Constitutional Violations: The Fourth Amendment protects against unreasonable searches, and 24/7 location tracking certainly qualifies.
Consumer Protection Violations: Embedding surveillance in consumer products without disclosure violates consumer protection laws in virtually every jurisdiction.
Federal Criminal Law: The Computer Fraud and Abuse Act (18 U.S.C. § 1030) and Electronic Communications Privacy Act (18 U.S.C. § 2511) criminalize unauthorized access to electronic devices and communications.
The legal framework to stop this surveillance exists. What we need is evidence, and Brutus has shown us how to collect it.
The Cover-Up Begins
As Brutus’ investigation progressed, something disturbing happened. Other researchers who had been documenting the same surveillance system began changing their stories. The Australian researcher who had been collaborating suddenly claimed it was “just advertising” and refused to discuss the technical evidence.
When Brutus challenged this narrative flip, the researcher went silent.
Then came the intimidation. Someone with advanced technical capabilities contacted Brutus, demonstrating they could track his digital identity across platforms in real-time. They showed him his Telegram ID, his username, and how his online activities were being monitored.
Brutus’ response was characteristically blunt: he told them to “f*ck off.”
But the message was clear: powerful actors were now paying attention to his investigation.
The Economic Reality Check
Brutus made a brilliant observation that destroys the “advertising” cover story: the people being surveilled in his Central American town make $600-900 per month. They can “barely feed their families or pay rent” and are “lucky if they can take the family for pizza after paying bills.”
No rational advertising company would invest in expensive, illegal surveillance infrastructure to target people with no disposable income. This surveillance serves a different purpose entirely, population control, behavioral research, or social engineering.
The fact that this system is being deployed in developing nations first suggests we’re witnessing a testing ground for global surveillance infrastructure. Perfect the technology on populations with limited resources to resist, then scale it up worldwide.
What You Can Do Right Now
Here’s the most important part: you can verify this yourself in the next ten minutes.
Brutus’ discovery is reproducible by anyone (I did it) with a smartphone. Here’s how:
For Android Users:
- Download “BLE Scanner” from the Google Play Store (by Bluepixel Technologies)
- Grant all permissions (Bluetooth, Location, Storage)
- Open the app and let it scan for 10 minutes
- Look for devices with long, weird names like “C108B094370702…”
- Check if these devices show “Unknown” manufacturer
For iPhone Users:
- Download any BLE scanner app from the App Store
- Follow the same process
- Document any suspicious devices you find
What to Look For:
• Long alphanumeric device names (usually starting with letters like C1, 74, or 15)
• “Unknown” or unregistered manufacturers
• Devices that appear consistently in the same locations
• Strong signal strength from devices you can’t physically locate
If you find these devices, you’ve just documented evidence of the surveillance system in your own neighborhood.
Why Public Action Is Essential Now
The window for action is closing. Brutus made a crucial observation: the surveillance infrastructure exists, but it may not yet be fully operational. The system requires massive AI processing power to analyze the movement and behavior of millions of people simultaneously.
But AI capabilities are advancing rapidly. The same companies building this surveillance infrastructure, Google, Apple, Amazon, are racing to develop AI systems powerful enough to process surveillance data at global scale.
We may be in the final window before this system becomes fully operational and unstoppable. Once AI reaches the threshold for mass surveillance processing, the infrastructure Brutus discovered could become the foundation for total population control.
Previous privacy settlements have failed. Facebook paid $5 billion to the FTC and $725 million in class action settlements for Cambridge Analytica, yet continues surveillance unchanged. Google has paid hundreds of millions in location tracking settlements, yet the tracking continues with minor policy adjustments.
Individual legal action isn’t enough. The surveillance system operates globally, across multiple jurisdictions, through corporate partnerships that transcend national boundaries. Only coordinated global resistance can expose and dismantle it.
Regulatory agencies need evidence. The FCC, EU data protection authorities, and other regulatory bodies have the power to stop this surveillance, but they need documented evidence of violations. Brutus has shown us how to collect that evidence.
Democracy depends on privacy. When every person’s movements, associations, and behaviors are monitored in real-time, political organizing becomes impossible. Economic freedom disappears when algorithmic systems control access to opportunities. Social relationships become mediated by surveillance algorithms.
This isn’t about individual privacy, it’s about whether we live in a free society or a technological prison.
The Global Verification Project
Brutus’ evidence is compelling, but it’s just one person in one location. To expose this system globally, we need what I’m calling the “Scan Your Area” verification project.
Imagine if 100,000 people across 100 countries all scanned their areas and documented surveillance devices. Imagine if this evidence was collected systematically and presented to courts, regulators, and lawmakers worldwide. Imagine if we could prove this surveillance system exists everywhere, operating illegally, violating the privacy of billions of people.
This isn’t theoretical. Brutus has provided the methodology. The tools are free and available to everyone. All we need is enough people willing to spend ten minutes proving what’s happening in their own communities.
The evidence would be irrefutable. Unlike previous privacy scandals that relied on internal documents or whistleblower testimony, this evidence can be collected independently by anyone with a smartphone. Courts can’t dismiss it. Regulators can’t ignore it. Companies can’t deny it.
The legal impact would be unprecedented. With documented evidence from multiple jurisdictions, we could file coordinated lawsuits under FCC regulations, privacy laws, and constitutional protections. The violations are clear, the evidence is reproducible, and the legal framework exists.
The public awareness would be transformative. When millions of people discover surveillance devices in their own neighborhoods, the abstract concept of “data privacy” becomes personal and immediate. Public pressure for action becomes unstoppable.
What Happens Next
I’m looking into working with privacy advocates, legal experts, and technology professionals to launch a global “Scan Your Area” campaign. The goal is simple: get enough people scanning and documenting surveillance devices that the evidence becomes undeniable and the pressure for action becomes unstoppable.
This isn’t about convincing people to believe something. It’s about giving people tools to discover the truth for themselves.
This isn’t about individual compensation. It’s about collective action to eliminate surveillance entirely.
This isn’t about trusting experts or authorities. It’s about citizens taking control of their own privacy and freedom.
If you scan your area and find nothing suspicious, that’s valuable data too. But if you find what Brutus found, illegal surveillance devices broadcasting in your neighborhood, then you’ve just become part of the most important privacy investigation in history.
The Choice We Face
Brutus’ investigation has revealed something extraordinary: we have a choice.
The surveillance infrastructure exists, but it may not yet be fully operational. The legal framework to challenge it exists. The tools to document it are freely available. The evidence is reproducible by anyone with a smartphone and ten minutes.
We can expose this system before it becomes unstoppable. We can force accountability through legal action. We can demand that our devices serve us, not spy on us. We can choose a future where technology enhances human freedom rather than destroying it.
But only if we act now.
The alternative is a world where every movement is monitored, every relationship is tracked, every behavior is predicted and controlled by algorithms. Where resistance becomes impossible because it’s detected before it can organize. Where freedom becomes a memory of what life was like before the machines started watching.
Brutus took enormous personal risks to document this surveillance system. He lives in a place where “life is worth $40 on the street,” where armed visitors have appeared at his home, where researchers are being intimidated or compromised.
He did this because he understood something crucial: if we don’t expose this system now, we may never get another chance.
Your Move
The least we can do is spend ten minutes scanning our own areas and documenting what we find.
Download a BLE scanner app right now. Turn on Bluetooth. Look for devices with weird names and “Unknown” manufacturers. Take screenshots. Share what you find.
It’s that simple. And it might be the most important thing you do this year.
Because Brutus is right about one thing: this is military-grade technology deployed against civilian populations. The question is whether we’re going to let it operate in secret, or whether we’re going to drag it into the light and demand accountability.
The choice is ours. But only if we make it now.





Leave a Reply
You must be logged in to post a comment.